Opening Up The Discussion on DaC
As the threat landscape continues to expand and cybersecurity professionals face more threats every day, they look to utilize methods to cover larger swaths of the boundary more quickly, simply, and securely. Detection-as-Code is one such effort being expanded on and utilized across a variety of security tools.

The History of DaC & A Plausible Timeline For How We Got Here
================================================================
Snort
 DaC gets its origins from the ideas behind Snort all the way from 1998. Snort is an open-source Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) which utilizes community rules and paid rules to detect and prevent network intrusions. This community approach to defense is still prevalent today across the industry. Snort, which was created by the founder and former CTO of Sourcefire (purchased by Cisco in 2013), is now maintained by Cisco but still offers its open source community and paid rulesets.
DaC gets its origins from the ideas behind Snort all the way from 1998. Snort is an open-source Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) which utilizes community rules and paid rules to detect and prevent network intrusions. This community approach to defense is still prevalent today across the industry. Snort, which was created by the founder and former CTO of Sourcefire (purchased by Cisco in 2013), is now maintained by Cisco but still offers its open source community and paid rulesets.
Suricata
 Next onto the scene came Suricata in 2010 (1.0 release) who was looking to address some of the issues with Snort, primarily surrounding the handling of large volumes of information. Over the years, Suricata has become central to many various offerings across the industry and is utilized directly by many more. Suricata places itself in more of a broad "Network Security Monitoring" position as opposed to simply an IDS/IPS.
Next onto the scene came Suricata in 2010 (1.0 release) who was looking to address some of the issues with Snort, primarily surrounding the handling of large volumes of information. Over the years, Suricata has become central to many various offerings across the industry and is utilized directly by many more. Suricata places itself in more of a broad "Network Security Monitoring" position as opposed to simply an IDS/IPS.
YARA
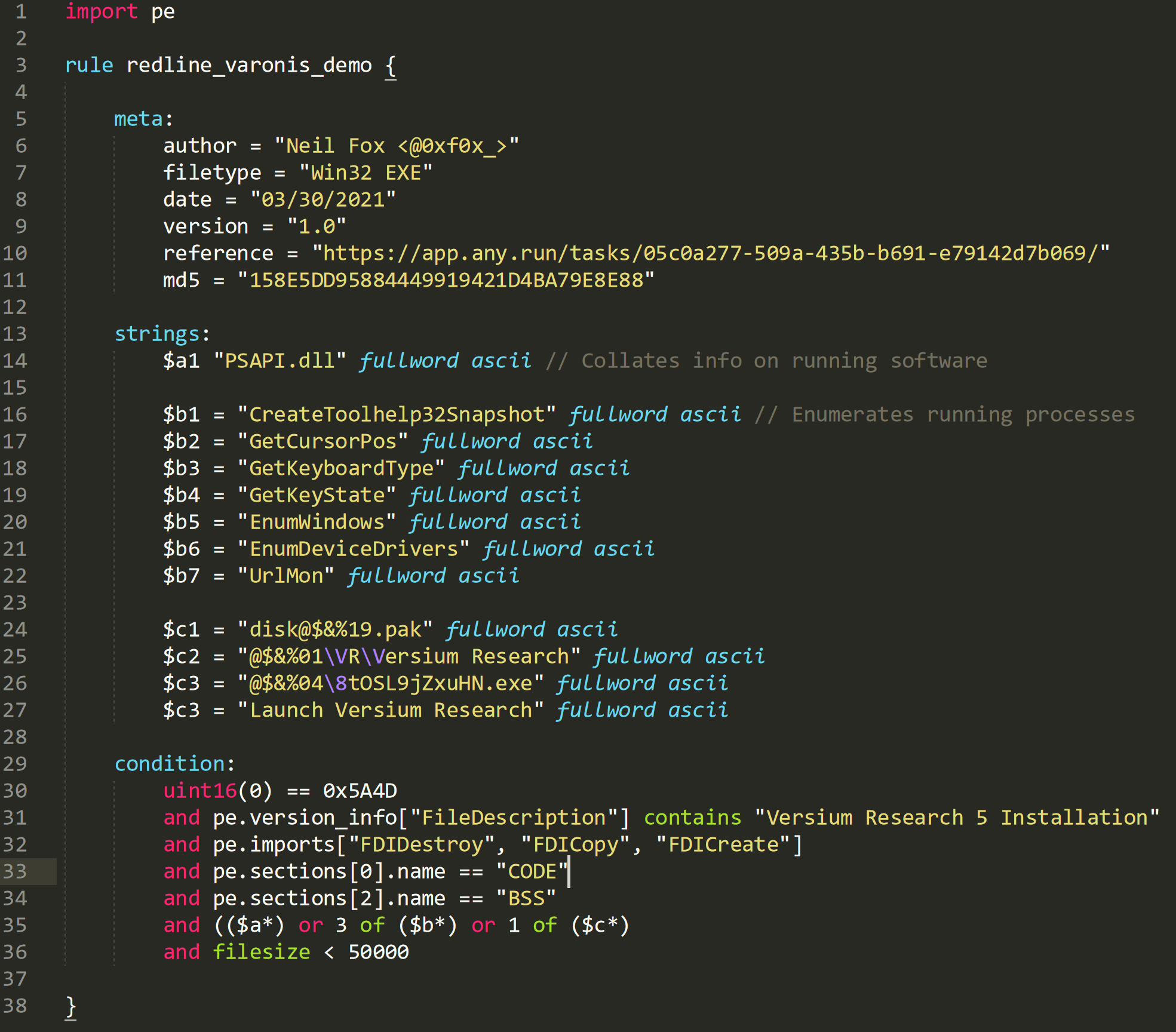 In 2013, Victor Alvarez of VirusTotal released YARA rules on GitHub. YARA rules are utilized for fingerprinting malware by defining the various patterns contained in a piece of malware. Since its inception, YARA rules have been widely used in the industry for identifying and protecting from known malware variants.
In 2013, Victor Alvarez of VirusTotal released YARA rules on GitHub. YARA rules are utilized for fingerprinting malware by defining the various patterns contained in a piece of malware. Since its inception, YARA rules have been widely used in the industry for identifying and protecting from known malware variants.
A Brief Look at the Present
From the rise of cloud compute to the push to serverless architectures, more and more of the stack is being code-ified. The cybersecurity stack is no different. From infrastructure-as-code to now detection-as-code, the ability to have solutions which allow for more control in a programmatic method, is being prioritized due to the ability to quickly deploy and compartmentalize operations. Some of the benefits to this methodology are that you can implement software engineering best practices into a CI/CD pipeline across your organization, you can version control and quickly rollback just the pieces and parts you need to, and you can automate the repetitive aspects of this process to drive efficiencies.
 The world is not a set-it-and-forget-it place, as much as Ron Popeil may have had you convinced. The show must go on, so the benefits of the continuous improvement via code-ifying your stack allow you to continuously improve in a structured process and to simplify collaboration across the organization and the industry.
The world is not a set-it-and-forget-it place, as much as Ron Popeil may have had you convinced. The show must go on, so the benefits of the continuous improvement via code-ifying your stack allow you to continuously improve in a structured process and to simplify collaboration across the organization and the industry.
The Case for Collaboration Across the Industry
================================================================
One solution that sparked some thoughts for how the industry could collaborate and improve security postures across organizations was the approach taken by Sublime Security who takes the Detection-as-Code mindset and applies it to email security. Email is still one of the most popular attack vectors of an organization and that's because humans are at the other end and humans want to trust.
When looking at how Sublime handles collaboration/detection rule sharing, it immediately made me imagine the US Government agencies all having instances of Sublime and sharing rules back/forth with each other automatically - once one agency sees the technique, detection rules can be built out and shared across all agencies. Additionally, with threat hunting and pen testing teams at these agencies, the possibilities of this solution are immense.
Another benefit to this solution is that you know how the solution is going to respond before the time comes for it to respond due to the fact that it's not a black box and the detection rules are built out or subscribed to by every instance owner.
Already, many of the users of Sublime are sharing their detection rules in the community and this allows others to benefit from the TTPs observed by others.
But how do we apply this thought process to other areas of cybersecurity? What is the next area of cyber that can be code-ified?